IMPLEMENTATION OF E-GOVERNMENT IN MALAYSIA
IMPLEMENTATION OF E-GOVERNMENT IN MALAYSIA
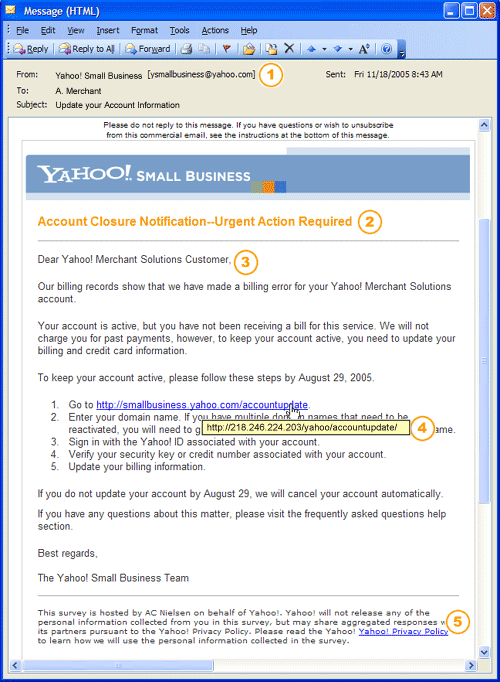
The status of e-government implementation in
The e-government initiative launched the country into the Information Age. It will improve the government operates internally as well as how it delivers services to the people of
In order to realize the e-government adoption in
E-government is one of the seven flagship applications introduced in MSC. Under the e-government flagship, seven main projects were identified to be the core of the e-government application.
1) Generic Office Environment (GOE)
-- The aim of GOE is to introduce a fully integrated, distributed and scalable office environment that leverages use of the multimedia information technology.This will enable efficient communication, allowing collaboration across all workers, and ensuring right information reaching the right people in the timely manner.
2) Electronic Procurement (eP)
-- The aim is to re-engineer, automate, and transform current procurement system. The project would cover central contract, tender, and direct purchase. Besides that, the use of eP will increase transparency, save time and money while encourage suppliers to go electronic and join the K- Economy.
3) Human Resource Management Information System (HRMIS)
-- The introduction of HRMIS as an e-government project will provide single interface for government employees to perform human resource functions effectively and efficiency. Furthermore, it will help to standardize all human resource processes for federal, state, statutory body, and local authority services. The objective of HRMIS is not just for record keeping but also provide transactional functions such as leave application, loan processing, competency management, recruitment, and selection of employee.
4) Project Monitoring System (PMS)
-- This projects will create a mechanism to monitor project implementation throughout various government agencies and statutory bodies. PMS also provide a platform to exchange ideas and to demonstrate best practices in information management and communication services. The PMS is designed to provide a mechanism for monitoring the implementation of government projrct ("Pilot Projects", n.d.). The service also provides a platform for exchanging ideas and demonstrating best practices models in information management and communication services.
5) Electronic Services Delivery (eServices)
-- This project is a pilot project that allows citizens of
6) Electronic Labor Exchange (ELX)
-- This project is to improve the mobilization of human resources and optimize work force utilization through systematic matching of job seekers to job vacancies. As such, this would enable the Ministry of Human Resources (MOHR) to be one- stop centre for labour market information that will be accessible to the public.
7) E- Syariah
-- This project is to improve the quality of service in Syariah courts. This will eventually enhance the Islamic Affairs Department’s effectiveness through better monitoring and co-ordination of its agencies and improving the management of its 102 Syariah courts. The E- Syariah application consists of Syariah Court Case Management System , Office Automatic System, E- Syariah Portal, Syarie Lawyers Registration System and Library Management System.
.
CITIZEN'S ADOPTION OF E-GOVERNMENT
Citizens expect and demand governmental services with a high degree of quality, qua ntity, and availability in a 24-hour, seven-days-a-week, and year-round fashion. Success in delivering electronic services depends upon the capability and self-confidence of citizens in performing e-transactions, as well as their trust and confidence in the protection of their personal data within an open and accountable government.
ntity, and availability in a 24-hour, seven-days-a-week, and year-round fashion. Success in delivering electronic services depends upon the capability and self-confidence of citizens in performing e-transactions, as well as their trust and confidence in the protection of their personal data within an open and accountable government.
Influence citizens’ adoption of e-Services is very important, because the success and acceptance of e-Government initiatives are dependent on citizens’ willingness to adopt and utilize these services.
Perceived ease of use, compatibility, and trustworthiness are significant predictors of citizens’ intention to use e-Services and that perceived reactive advantage, perceived image, perceived compatibility, perceived usefulness, and relative advantage are significant elements of e-Government adoption.
Most users used E-Government websites in their workplace and the most frequently used topic was taxation.Information quality and system quality are significant factors that influence the adoption of E-Government websites. Accuracy, relevancy, and completeness were more significant than timeliness and precision. Efficiency was the most significant factor.